When developing a security strategy, businesses must plan to protect against not just current threats, but all threats, known and unknown.
Existing Security Threats don’t go away….Many businesses and end users remain susceptible to a myriad of known attacks due to a simple failure to patch known vulnerabilities, out-dated equipment and malware signatures, or a failure to properly setup and deploy security devices.
The evolution of new threats are increasing….The Internet’s standards-based web interface and incredible number of applications have made it the primary choice for hackers and thieves looking for new ways to steal information, disrupt services and perform other malicious activities for financial gain. Corrupting computers and networks, and stealing personal data through web-borne viruses, worms and Trojan applications is now commonplace. Ever increasing sophisticated attacks leverage technology and social engineering to trick users into executing malicious activity that harvest confidential information. The most prevalent threat types include spyware, phishing, instant messaging, peer-to-peer file sharing, streaming media and social media. The resulting number of data breaches, including identity theft, credit card information theft, fraud, etc. increase every year and cause real damage.
Both consumers and business are adopting social media applications including Twitter, Facebook, and YouTube into their everyday business practices at a rapid pace. These Web 2.0 applications enable instantaneous, always-on communications between employees, business partners and even temporary contractors, bringing the opportunity for great leaps in productivity and increasing profits.
As might be expected, allowing these consumer-oriented applications with user-generated content into the enterprise raises a myriad of security concerns.
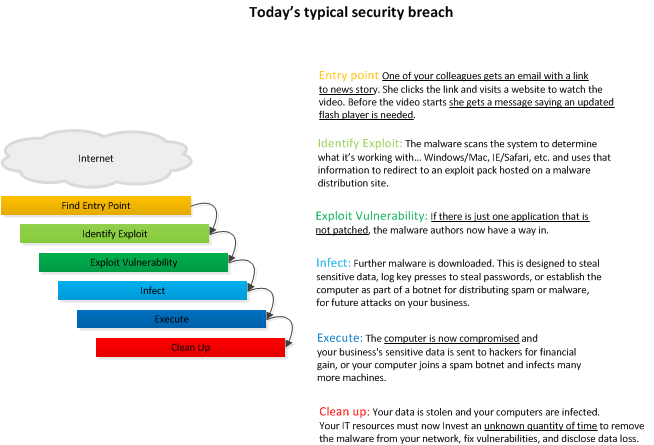
What does a typical attack look like?
Traditional firewalls are no longer effective….Traditional stateful firewalls with packet filtering capabilities used to be highly successful at blocking unwanted applications simply because most applications communicated over networks by using specific and unchanging computer ports and protocols. Traditional port-based protection is no longer practical. For example, blocking port-80 would block access to the web entirely, and this is simply not an option for businesses today.
Next-Generation Networks…For many businesses, their existing networks are not adequate to support their long-term and sometimes even short-term growth plans. These next-generation networks are being tasked with demanding needs; from providing large branch offices or mobile workers with secure access to critical corporate information, to powering virtualised data centres and low-latency cloud-based applications, to delivering reliable high-quality business and security services to multiple globally dispersed customers. Next-generation networks must be flexible enough to simultaneously support high volumes of traffic as well as rich media protocols without slowing down.
In order to maintain high throughput and reliability, these complex networks must have security devices that won’t become chokepoints as they inspect and filter traffic for threats and malware.
Next Generation Security Platforms…As enterprises evolve to more complex networks higher data rates and traffic volumes, they require highly flexible security platforms that can evolve and scale. Businesses need next-generation security platforms and related devices that are flexible enough to provide protection against both known and unknown threats, while scaling to accommodate business growth and new services.
Your next generation security platform must cater for traditional firewall security requirements as well as offer additional functionality such as Application Control, Intrusion Prevention Systems, Data Loss Prevention Capabilities and Web Content Filtering.
If you’re not adequately protected in this new world of internet delivered services, the likelihood of attack is high and the cost will be significant.









Leave a Reply
You must be logged in to post a comment.